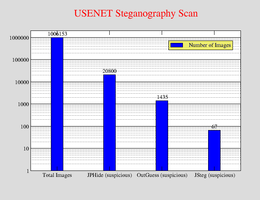
Image Statistics
Graph created at November 3 2001 06:20:30 PM
Stegdetect is being used for the classification. Stegdetect determines a statistical likelihood for hidden messages. There is no guarantee that an image contains a hidden message.
All suspicious images are being processed by stegbreak.
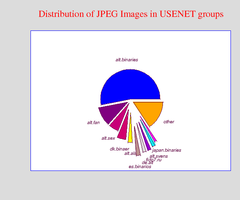
Image Distribution in USENET groups
Graph created at December 21 2001 05:04:04 PM
The distribution is heavy tailed and group hierarchies not shown by name are reflected by category other, about 16% of all images.
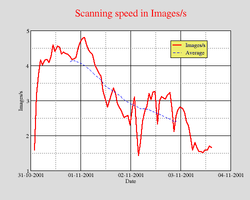
Scanning Statistics
Graph created at November 3 2001 06:20:30 PM
One spool file is about 125 MByte large and contains a few hundred images.
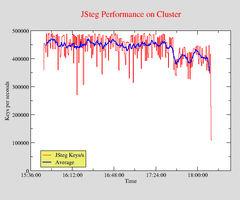
Stegbreak Statistics: JSteg
Graph created at October 17 2001 05:39:35 AM
Disconcert distributed the job on 16 workstations. At the end of the run, one of the workstations dropped out.
The dictionary attack on JSteg did not find any messages.
Stegbreak Statistics: JPHide
The graph shows the speed with which the fourth quarter of the JPHide positive images are beeing processed by Stegbreak.Disconcert distributes the job on about two hundred workstations. The cluster has a peak performance of about 870,000 keys per second. The speed is comparable to approximately seventy-two 1200MHz Pentium III workstations or 87 GFLOPS as a rough estimate.
The jobs run mostly on workstations provided by CAEN, MIT and CITI.
We did not find any hidden messages while processing the JPHide positive images.
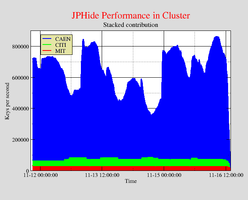 | 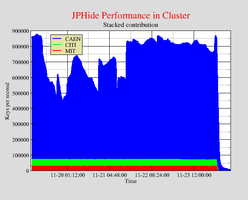 |
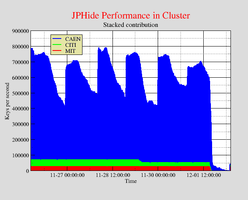 | 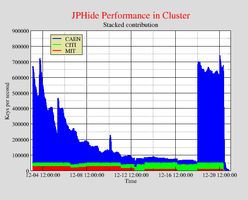 |
Graph created at December 21 2001 05:22:35 PM